MITM Attack (Packet Sniffing Attack)
We will see the full process of how to perform the MITM attack with all the steps [Note:- before performing the MITM attack you should know the IP & MAC address of Windows system(Victim), Kali(your machine from where attack will be done) & Router(In which you and your target machine are connected)] :-
STEP 1 :- Open kali linux root terminal and
type the following command :-
Ettercap -G
STEP 2 :- Now click on the ‘✓’ mark and new window will pop-up :-
In which select hosts and tap on scan for hosts:-
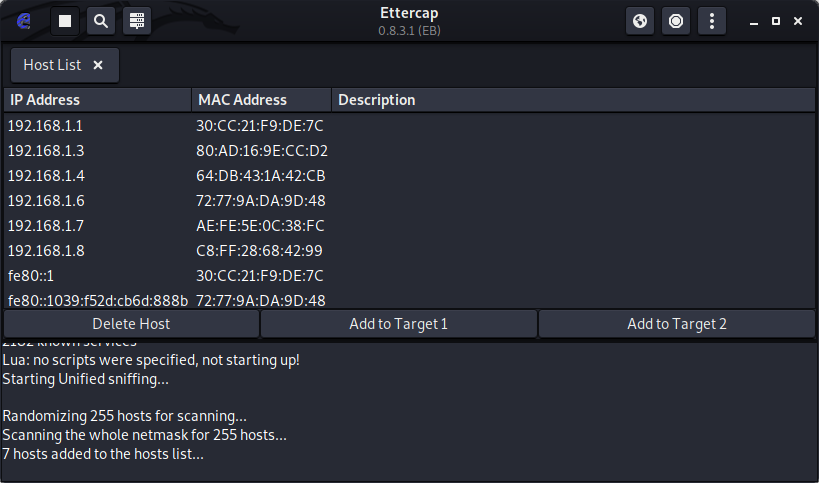
Now select hosts list from options :-
STEP 3 :- Now you can see that there are various hosts are available in the hosts list:-
STEP 4 :- From that list select the IP address of you router and add it to the target 2 & windows(victim IP) to target 1 and now click on the globe like icon and you will see the list which is shown below in which choose the ARP poisoning option:-
Now click on OK after the window gets pop-up:-
STEP
5 :- Now
open Wireshark in kali linux terminal by typing
wireshark
and a window will
pop-up in which you can choose eth0
or any to see
the packets:-
STEP 6 :- Now click on eth0 or any and if we choose eth0 then now if Victim(Windows machine) opens any browser it will show us the packets that are been captured amd if we choose any then if Victim(Windows machine) opens anything even if files we will see that packets are capturing and you can also see the protocol by clicking on a particular packet and you can also discover more by right clicking the packet to get more options :-










Comments
Post a Comment